As our technology evolves, so must our legal system. With the advent of biometrics and advanced decryption methods, law enforcement agents are becoming accustomed to obstacles regarding laws that haven’t yet been updated for 2019. Navigating these laws with new technology like Apple’s Face ID and various adaptations of fingerprint authentication isn’t easy, and law enforcement’s decision-making process can depend on the situation at hand.
Social media sites, online forums, and shared platforms allow users to communicate faster and with more people than ever before, making these mediums the new marketplace for ideas and communication.
Given the information that technology companies are privy to as a result of the goods and services they provide, the government frequently requests data to help with investigations and matters of public and national security.
Technology companies elect to make this information public in the form of “transparency reports,” which are usually updated every six months. These information requests can come in multiple forms, including subpoenas, search warrants, wiretap orders, pen register/trap and trace orders, and others, including requests from foreign governments.
However, these companies are not forced to comply with all of the requests. Rather, they review them and comply as they see fit, based on the context of the request and user privacy agreements. Corporate transparency, whether sharing how companies respond to these requests or otherwise, is important for consumer trust.
The findings below are garnered from United States-specific portions of transparency reports from select technology companies.
Information Requests Are Rising Among Large Telecommunications Companies
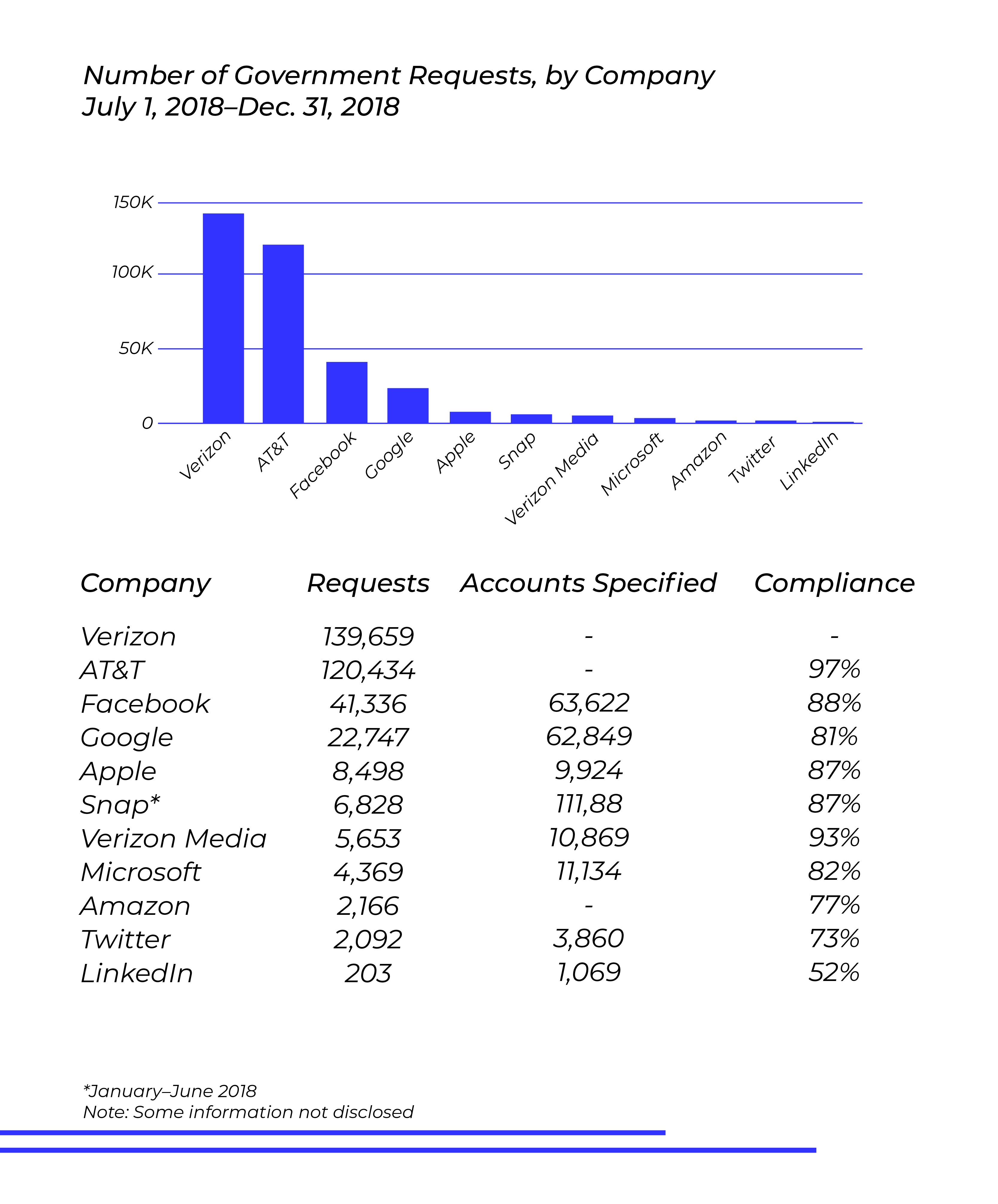
Unsurprisingly, telecommunications giants such as Verizon and AT&T led the pack by a wide margin, accounting for over 260,000 requests in the final six months of 2018. This can be attributed to the fact that federal and local law enforcement agencies have recently been looking into information related to cellphone calls and location data. The issue of cellphone encryption came to light after the FBI formally submitted orders to compel Apple to bypass the encryption protections on one of the 2016 San Bernardino tragedy perpetrators’ work cellphones.
From that day forward, the discussion concerning business cooperation in federal investigations has become more nuanced. As the line between the desire to protect people’s privacy and uphold justice becomes more blurred, other telecommunications and social media companies such as Facebook and Google have become a part of the discussion.
These tech mammoths are just two of the companies actively protesting governmental regulation on this scale. In Australia, for example, recently passed laws have given the government the ability to put pressure on tech companies with formal requests of varying degrees, and even include a section that requires companies to develop and build new decryption technologies.
Due to the rise of encryption requests, companies with fewer requests such as LinkedIn will likely see a rise eventually, with the possibility of new federal standards blanketed across all businesses.
Requests vs. Forced Compliance Comparison
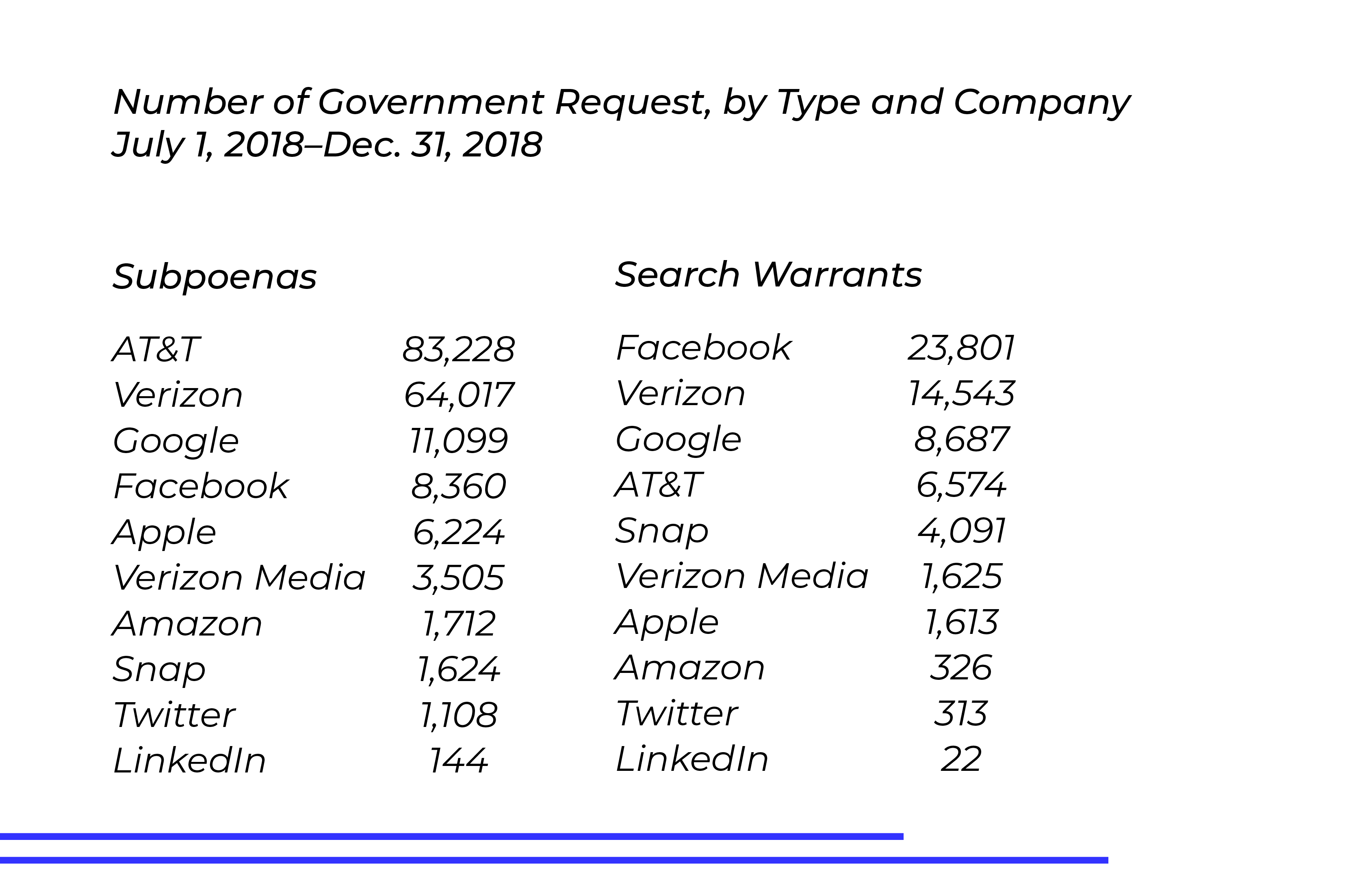
Although AT&T’s cumulative subpoenas surpassed Facebook’s total on a nearly 10-to-1 scale, in the final six months of 2018, Facebook pulled ahead of Verizon and AT&T for the most search warrants delivered by government agencies. Facebook was served over 3.5 times more search warrants than AT&T during the same period.
Outdated laws that no longer apply to the digital age are prompting new court cases that take on the issue of encryption, setting new precedents for what content is considered admissible.
Requests Are Continuing to Rise Astronomically
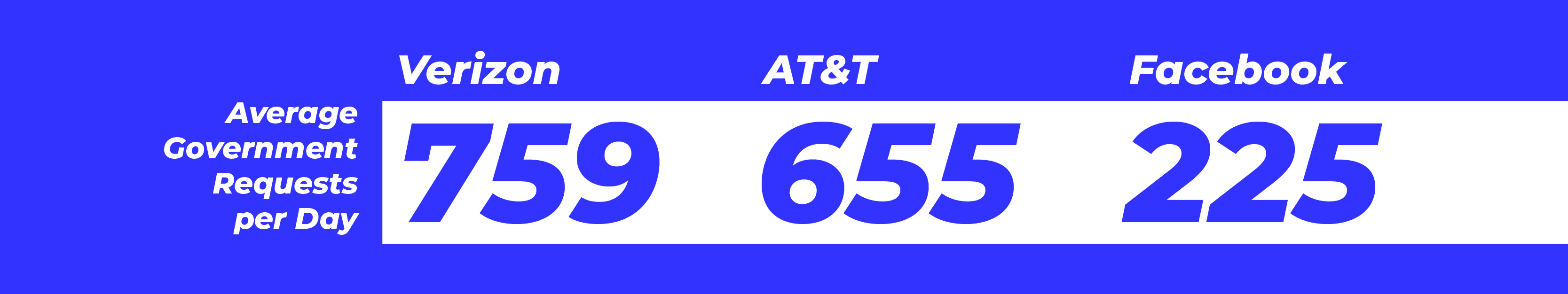
The number of government requests is staggering, and it probably takes a small army of people to review and respond. Looking at total requests for the latest six-month period, the data shows that Verizon and AT&T received an average of 759 and 655 requests per day, respectively.
These numbers reflect how much of our communication occurs online. This type of corporate transparency allows for vulnerability but also gives companies the ability to address these requests publicly. Many criminals boast about their crimes on social media, some even taking it to the extreme. Those behaviors could be cracked down on and subsequently phased out as the legal system and police adapt to the changing ways we share and consume information.
Twitter Requests Are on the Rise as Threatening Incidents Increase
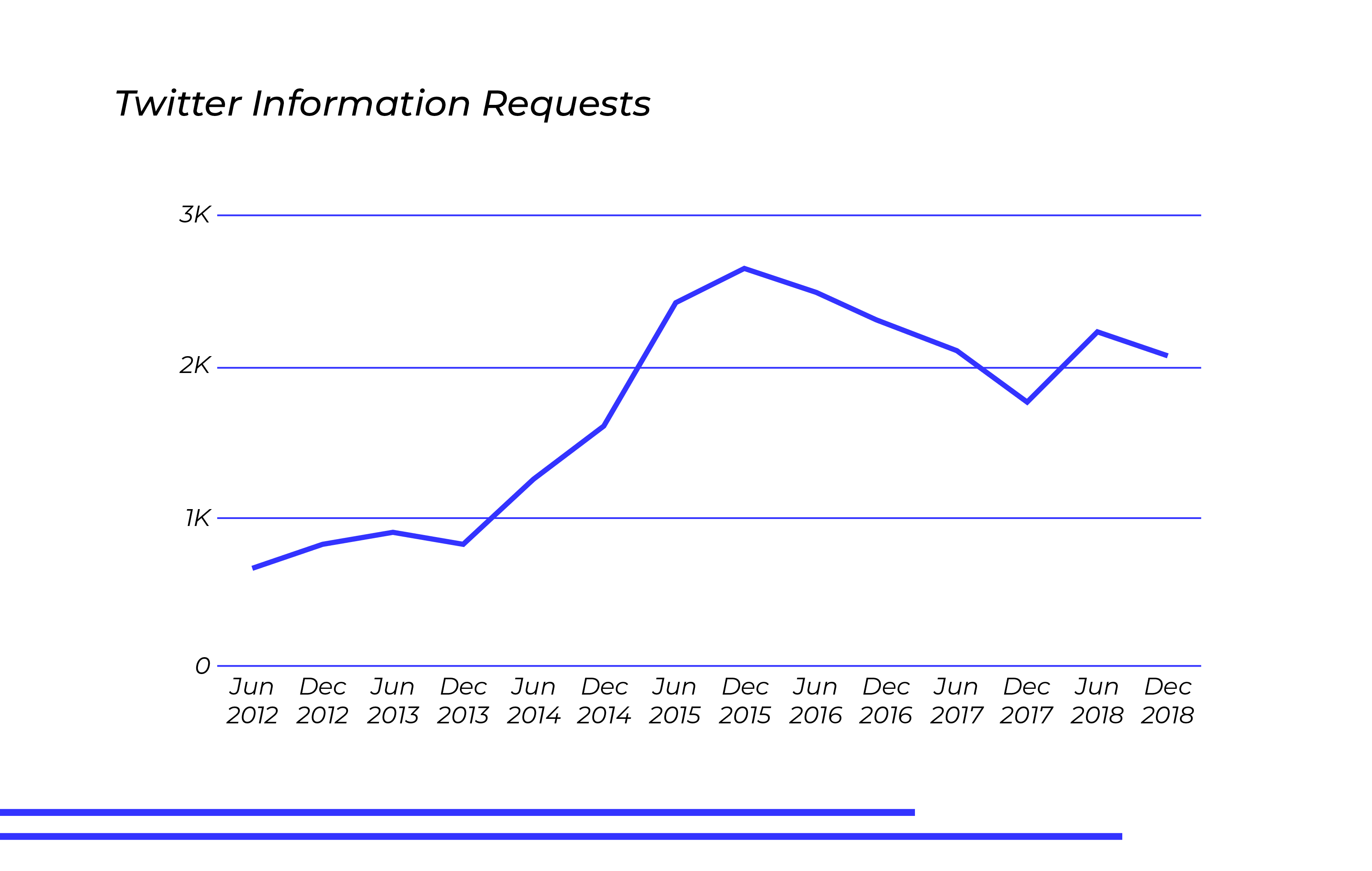
Looking exclusively at Twitter’s annual reports for account information requests, we observed a clear increase in volume since 2012.
The U.S. government now submits nearly a third of the global information inquiries that Twitter receives. Twitter shares this data annually via a transparency report that highlights key statistics about its information requests, including emergency request compliance numbers.
Nevada, California, and Virginia Lead Twitter Information Requests
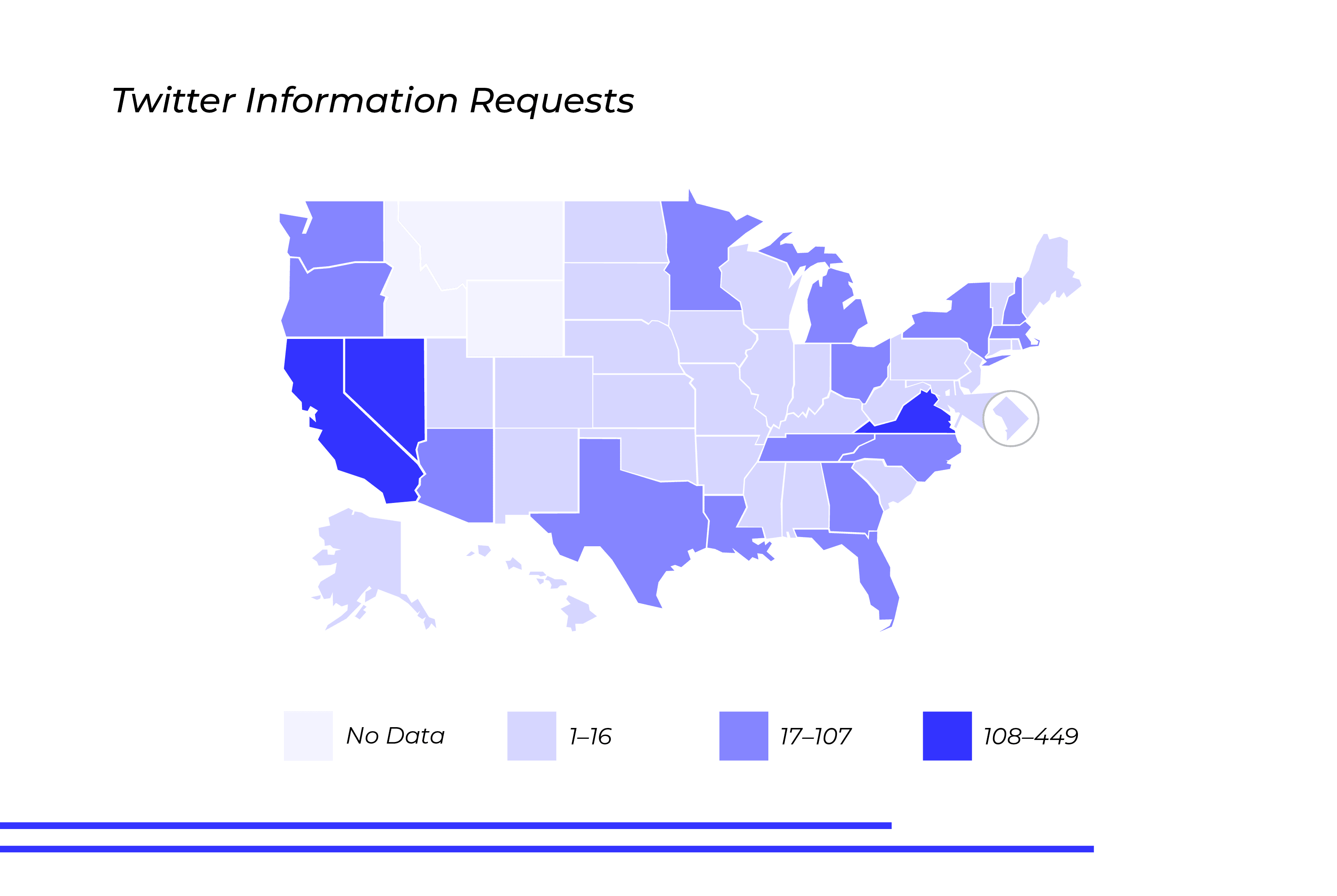
Breaking the Twitter information down by geography, the states with the most requests included Nevada, California, and Virginia. Among those states, internal data showed that Los Angeles County, California, and Manassas City County, Virginia, led the way, with 27% and 22% of total state requests coming from those counties, respectfully.
California has embraced new regulations aimed at identifying “Twitter bots” to alert users that the account is not “natural” or that it could be part of an account mill scheme or an intentionally automated page. Many of the nefarious and threatening profiles on the networking site are bots, giving Twitter incentive to cooperate, as the regulation would help protect users from behavior that violates its terms of service.
Top Reasons for Removing Content on Google

In many cases, governments or departments request that content be blocked or removed. Google releases the selected reason for removal. In total, it received 1,002 requests from Jan. 1, 2018, to June 30, 2018. Defamation constituted the largest percentage of requests at nearly 66%.
Defamation cases can come in a variety of forms, from innocuous stray comments about celebrities to cases in which people get hurt. Protecting your identity and your namesake is becoming increasingly harder on the internet, but taking legal action can help you stand your ground against inflammatory statements.
Other grounds for consideration were fraud (15%) and bullying/harassment (almost 6%). Cyberbullying is increasing year after year, even with more awareness about the issue and with initiatives from the White House.
Conclusion
Businesses of all types – not just the telecommunications industry – will eventually need to think about encryption. Keeping your data safe should be a priority. With proposals to set up “backdoor entrances” so that the federal government can access millions of social media and internet users’ private data, plus experimental techniques to gain information against criminals, it’s important to view this issue from both sides. While companies and their users value privacy, law enforcement is interested in public safety and justice.
Curious about learning more about the legal process? Visit Lawsuit.org today to learn more about your rights.

Fair Use Statement
We encourage you to freely share this content and ask that if you do, please reference this page as the original source.
